|
Shanghai Baudcom Communication Device Co.,Ltd
|
64-Bit Multi-Core Flow-Control Gateway Routers
| Price: | 2000.0 USD |
| Payment Terms: | T/T,L/C,D/A,D/P,WU,Paypal,Money Gram |
| Place of Origin: | Shanghai, China (Mainland) |
|
|
|
| Add to My Favorites | |
| HiSupplier Escrow |
Product Detail
64-Bit Multi-Core Flow-Control Gateway Routers
Overview
BAUDCOM 7300 gateway series are 64-bit MIPS multi-core gateways developed by Shanghai Baudcom Communication Device Co., Ltd. As a new generation of cost-effective and comprehensive flow-control gateways, they have private ASIC switching chips and are used at advanced cases for large or medium enterprises, broadband communities, campus networks, or carriers.
BD-R7300 gateways are strong in data processing, flexible in a variety of mainstream bandwidth access environments and various in providing sound bandwidth distribution solutions, all of which are means of effective utilization of bandwidth resources. In addition, these products provide network behavior management, P2P control, VPN networking, firewall, ARP cheat prevention and vicious attack prevention.
These gateways integrate multiline, NAT sharing, security and elastic rate limit, so they are to users an all-in-one comprehensive solution with high performance, high reliability and high performance-to-cost ratio.
Main Characteristics
High reliability and stability
After over a decade years of research experience in the data communication network field and studious research on broadband user's requirements, BAUDCOM broadband solutions have won customers' trust in all respects, especially in hardware or software design and in systematic strong ability, and these routers can run reliably for a long time in harsh environments such as high temperature, poor ventilation and bad grounding.
Strong data-processing capability
BD-R7300 adopts the 64-bit MIPS multi-core processor and the private ASIC switching chip, so it has high throughput and a high performance-to-cost ratio. They secure the reliable and rapid operation of such kernel functional modules as NAT, VPN, P2P identification and control, and firewall in an environment of multi-user and large flow.
Flexible multi-WAN access
A maximum of 8 WAN ports can be used for networking; the access modes such as Ethernet, FTTB optical fiber, ADSL and cable are supported; the multiline policies such as "bandwidth nesting", "intelligent routing" and "master/standby" are supported.
Versified flexible flow-control policies
BAUDCOM flow-control gateways have adopted the advanced 7-layer characteristic code identification technology and various policy databases, so they can be used in the following application cases such as HTTP, MAIL, database, P2P download, VOD and VoIP. According to customers' requirements, they can limit applications with high bandwidth but low priority such as P2P and VOD, and first process those with the high priority and low bandwidth.
At the same time elastic and effective bandwidth distribution solutions can be set flexibly according to the customer quantity: when free, the network will increase the bandwidth for each customer automatically; when busy, the bandwidth will surely be averaged, not being over-preoccupied. The assisting strategies (i.e. big-flow host limitation mechanism, flow outburst factors and optional user punishment/limitation) bring various and feasible methods for network management.
Two BAUDCOM bandwidth distribution and control policies integrate with each other, greatly improving the bandwidth usage. In case of large flow, BD-R7300 gateways can guarantee those prior services in enterprise networks or cyberbars. Users can be provided an orderly, effective and secure network environment by these gateway series.
Various behavior management policies
They have the following functions:
l Identify and control common IM software such as QQ and MSN based on the application layer;
l Support the white list;
l Identify frequent P2P programs based on the application layer;
l Block relevant services and conducting rate limit;
l Shield the stock, entertainment or purchase website based on the policy database;
l Update the policy database freely online.
Multiple anti-attack policies
BD-R7300 series is strong in preventing attacks. It can make a correct statistics and detailed analysis on all types of packets such as ARP, IP, ICMP, TCP and UDP, so the attacks can be automatically prevented once they are found and the alarm information can also be provided for rapid fault locating and removing.
For ARP cheat, BD-R7300 gateways provide IP-to-MAC binding, ARP-to-SCAN technology and free ARP and other mechanisms to secure the intranet; If working with BAUDCOM private switching products, these routers can be armed with DHCP-Snooping. In this way, ARP cheat cannot hide itself and it is 100% sure that ARP cheat can be detected and prevented.
Perfect log management
BAUDCOM secure flow-control gateways can provide varies kinds of log information, including URL filtration, internet surfing recording and query, and vicious attack records. Hence, customers can further know the detailed running status of the whole network and locate and solve network faults.
All-around VPN functions
BD-R7300 series supports VPN protocols such as L2TP, PPTP, GRE, IPIP and IPSec, and provides encryption algorithms, so that an overall solution can be provided to the construction of the remote office, the mobile office and the virtual private network; they also have the hardware encryption unit in their CPUs and hence have a strong ability of encryption.
User-friendly Web page
A simple and clear Web graphic interface is provided for configuration, so you can easily operate it even you are not professional.
Most of all, all kinds of configuration navigation help you to master all kinds of core functions.
Life-long free software upgrade
The IOS system of network products, the supplementary 7-layer characteristic database and the security policy database, all of which are provided by BAUDCOM, have free download/upgrade services.
Technical Parameters
Model | BD-R7304 | BD-R7308 | |
Interface combination | Ports | One Console port 4 GE Combo ports that support two bypass groups 1 USB expended port | One Console port 8 GE Combo ports that support two bypass groups 1 USB expended port |
MAC cloning | Supporting MAC cloning in both the intranet and the public network | ||
Port mirror | Supporting 1-to-1 or multi-to-1 port mirroring | ||
Access mode | ADSL, optical fiber, Ethernet, cable | ||
Hardware configuration | Processor | 64-bit multi-core MIPS processor (12 cores) | 64-bit multi-core MIPS processor (12 cores) |
DRAM | 2GB, which can be expanded to 8GB | 2GB, which can be expanded to 8GB | |
FLASH | 16M, which can be expanded to 32M | 16M, which can be expanded to 32M | |
CF | 1GB, which can be expanded to 4GB | 1GB, which can be expanded to 4GB | |
Suggested number of hosts | 3000 to 4000 concurrent hosts | 5000 to 6000 concurrent hosts | |
Physical Characters | Size | 442mm×207mm×66mm | |
Temperature/Humidity | Temperature: 0℃-40℃; humidity: 10%-85%, no condensation | ||
Power source's characteristics | Voltage: 170~264VAC; Curent:10MAVoltage: -36~-72V | ||
Maximum power consumption | 90W | ||
Routing and backup | Routing protocol | Supporting direct-through routes, static routes and default routes | |
Policy routing | Supporting flexible application schedule policies | ||
Multi-WAN policy | Supporting bandwidth cascading, intelligent path choosing, primary and secondary WANs, etc. | ||
Link backup | Supporting auto switchover of multiple WANs | ||
Line monitor | Supporting the ICMP or DNS keepalive mechanism | ||
Network function | Address transfer | Supporting the dynamic/static NAT and PAT | |
Virtual server | Supporting static port mapping, special mapping (SNAT+DNAT) and the DMZ host | ||
NAT connections | Supporting to limit the total number of connections of the whole machine or of each user Supporting to limit the TCP and UDP connections respectively | ||
UPnP | Supporting UPnP | ||
DNS | Supporting DNS Client/Proxy Supporting the peanuthull DDNS client | ||
DHCP | Supporting DHCP server/client/relay | ||
PPPoE | Supporting the PPPoE server and conducting IP-to-MAC binding, account freezing and speed limitation Supporting the PPPoE client | ||
Page push | Supporting electronic whiteboard to turn over the HTTP pages and also supporting content customization | ||
NTP | Supporting the SNTP network clock protocol Supporting policy management based on period and single time segment | ||
QoS limitation | 7-layer filtration | Basing on the characteristic code on the application layer, identifying and controlling P2P download, VoD, HTTP and Email, and limiting or guaranteeing the bandwidth | |
Flexible speed limitation | Automatically judging whether the network is idle or busy and conducting flexible speed limitation according to different standards | ||
Grouping speed limitation | Making user groups and designating different policies of speed limitation | ||
Dynamic distribution | Automatically calculating the threshold of speed limitation | ||
Multi-WAN | Limiting the speed of each WAN | ||
P2P speed limitation | Supporting the identification of the P2P download or the VoD on the application layer and the corresponding rate limit without getting normal services affected | ||
User Management | Optional control policies such as user punishment, limitation and outburst flows | ||
Behavior management | Real-time communication | Supporting to block the IM software like QQ and MSN by one key | |
P2P application | Identifying and controlling ten kinds of P2P programs such as BT, Thunder, PPStream and eMule | ||
Website management | Supporting to block the entertainment, share and shopping websites by one key Supporting URL filtration and keyword filtration and so totally controlling user's access | ||
Priority service | Supporting to first process company's Emails, hot network games, common OA databases and self-defined flows (based on characteristic identification according to the application layer) | ||
Blacklist and White List | Supporting the blacklist and the white List so as to facilitate user's control | ||
Policy upgrade | Supporting free and online upgrade of the behavior management database | ||
Network security | Firewall | Supporting the ACL firewall and blocking many frequent viruses on the basis of IP and port | |
DMZ port | Supporting to redefine the WAN1 port as the DMZ port and implementing safe networking | ||
DoS attack prevention | Supporting to prevent SYN Flooding, UDP flooding, ICMP flooding and ARP flooding in the intranet and the public network | ||
ARP security | Supporting static ARP binding, dynamic ARP binding and free regular ARP transmission Supporting automatic monitoring and alarming of ARP cheat Supporting in-depth IMP filtration | ||
VPN | Supporting multiple VPN protocols ( L2TP, PPTP, GRE, IPIP and IPSec) as well as protocol nesting | ||
Management | Graphic interface | Supporting Web interface management and providing fast wizard Supporting BIOS-based simple Web page and emergency recovery at incorrect operations | |
Network management protocols | Supporting SNMP V1/V2/V3 Supporting syslog record and management | ||
Fault diagnosis | Supporting the detection mode of the ICMP packets | ||
Account management | Supporting the hierarchical management of account's rights so as to fully secure the network | ||
State monitoring | Supporting an overall and real-time display of the states of the port, system and user | ||
Typical Application
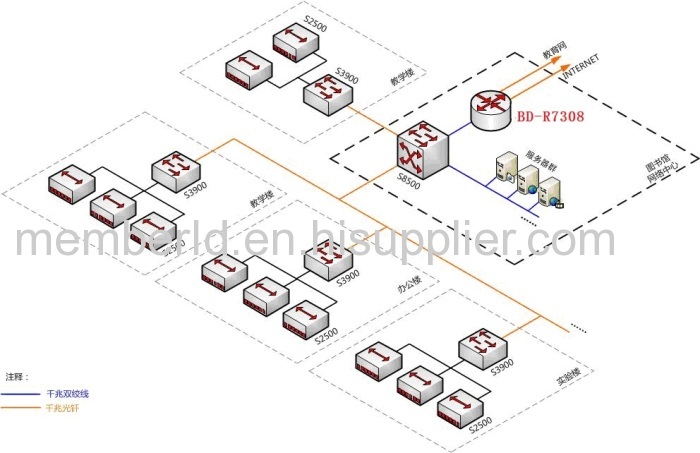
Application in the egress engine of a large-scale campus network
BD-R7300 NAT flow-control gateway series has 8 optical/electric multiplex interfaces, supporting load balance and multiple concurrent lines of communication carriers such as China Telecom, China Netcom and China Education Network.
BD-R7300 gateway series has a super data forwarding capability and a capability of creating and maintaining connections, so this series is the best solution to the large-flux network environment such as the egress of Education Network. BD-R7300 series has a creation speed of 300,000 connections per second, and a capability of stably maintaining large-flux connections, so they can provide stable support for those outburst overload network access requirements.
Moreover, BD-R7300 series also supports the elastic rate limit of user's bandwidth, the 7-layer application identification, the control of priority and service forbidding, DDoS attack prevention, user access record, event logs, etc.










